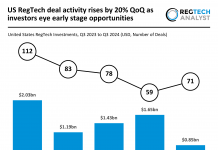
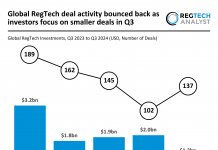
The National Security Agency (NSA) has published a set of best practices for organisations looking to bolster the security of their networks.
According to Security Week, this guidance is meant to be generic, applicable to a broad range of network devices and should help administrators prevent adversaries from exploiting their networks.
The NSA detailed organisations looking to ensure a network is protected from threats and that resources are secured should implement multiple defensive layers and also adopt a zero-trust security model.
The agency recommended organisations should install security devices such as a border router and next-generation firewalls at the perimeter and that publicly accessible systems and outbound proxies should be placed in-between firewalls, while monitoring solutions, redundant devices and remote log servers should be deployed within the network.
The NSA also remarked that admins should group together similar systems within the network and isolate them into subnets, applying proper network segmentation to ensure an adversary able to compromise devices that are most exploitable cannot reach other systems.
The NSA said, “Operational technology, such as industrial control systems, typically need to be isolated from other information technology and high-risk networks like the Internet. This physical separation provides stronger protection because the intermediate device between subnets must be compromised for an adversary to bypass access restrictions.”
Network security best practices also involve implementing access restrictions to critical internal network devices and a network access control solution, the NSA said. In addition, backdoor connections should be removed as well as the limiting and encrypting of VPNs.
Furthermore, administrators should properly configure authentication, authorisation and accounting and apply the principle of least privilege. They should also ensure administrative accounts are properly secured with unique usernames and passwords, credentials should be securely stored and they should disable unused accounts.
The NSA said that network security best practices also include proper file system and boot management, maintaining all software and operating systems updated and ensuring that in-use hardware is still supported by vendors. Remote logging and monitoring along with secure remote management of network devices should also be implemented.
Copyright © 2022 RegTech Analyst
Copyright © 2018 RegTech Analyst