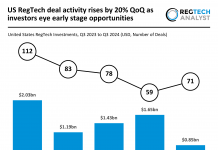
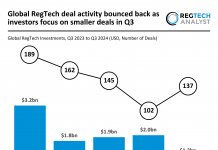
Despite them both occupying similar areas of security and defence, cybersecurity often resides in a separate world from governance, risk and compliance (GRC).
However, in a world that is becoming ever more deeply connected, is this the best way to still work? According to RegTech firm Diligent, there is a greater need to bring these two sectors together more.
“What if the information exposed in a data breach includes old policies about customer names, addresses and emails? You’ll need teams from both cyber and compliance to remediate the situation and mitigate risk moving forward. And what if the board is unable to answer lawmaker or investor questions about new cyber disclosures?” the firm said.
At a recent Summit, a panel of experts explored the growing intersection of GRC and cybersecurity, with tips for bringing these two worlds together successfully. This panel comprised Erin Lemky – Diligent director of global product marketing – Myrna Soto, who is CEO of Apogee Executive Advisors, and Redhorse Corporation CEO John Zangardi.
One of the key areas of cyber risks this year has undoubtedly been the geopolitical landscape, which has been rocked to its core by the war in Ukraine.
Zangardi said, “Whether you’re looking at Iran, Ukraine, or even a potential China-Taiwan Strait scenario, cyber will be a part of that. Because the United States has a vested interest in it and our allies are potentially targets, you are at risk.”
Diligent detailed that many organisations need strong GRC-related frameworks that integrate well with security.
“Compliance drives change – but it doesn’t make you more secure.” said Soto. She suggested “taking the GRC function just a step further” and using it to articulate how secure the organization is and how it’s mitigating risks.
In the opinion of Diligent, guided by the compliance frameworks for their organisation’s industry, GRC teams can work with security teams and management to understand and prioritise risk. The GRC team can work with their colleagues in cyber and IT to understand the scope of an organization’s cybersecurity framework and analyse its strengths and limitations.
Soto went on to define such risk management as “understanding our compliance positioning, understanding our regulatory positioning, understanding our cyber security program maturity and where the gaps exist.” Then team members report to the board “so that they have a clear understanding of where the company is, where their risks are, where they may be falling behind and why.”
Often, collaboration starts with culture. Zangardi stressed the importance of corporate culture in forging a partnership between cybersecurity and GRC, one that encourages working together to reach a goal. He said, “What doesn’t work is finger-pointing, being overly technical, or just checking a box.”
In a similar vein, Soto said that a culture of fear or shaming ‘alienates your partners, the same people you should be making relationships with in order to facilitate those objectives.”
Zangardi added, “It’s not easy, because trust just doesn’t happen overnight. It’s about understanding what you’re trying to achieve and working toward common goals.”
At many companies, compliance and GRC naturally fall under the purview of the audit committee. More and more, cybersecurity is joining this list.
Soto remarked, “We absolutely cover cyber in audit. What this does is help the audit team share and better understand the risks, because IT systems pretty much underpin every business.”
Read the rest of the post here.
Diligent has partnered with capital markets communications platform Q4 to provide pre-IPO and public companies with IR and board governance solutions.
Copyright © 2018 RegTech Analyst