The year anniversary for GDPR is coming up in May, but there are still a lot of confusion around certain aspects of the regulation, Compliance Compendium chief business development officer Gareth Gadd explains how using personal devices for work could cause problems.
Areas of data management which are still a little blurry include things like an assumed consent of how to use customers data. If a visitor ignores a pop-up box requesting whether they can have permission to use their data for cookies, for example, but they continue to use the website, is that in essence consent. This is just one of several blurred lines.
Compliance Compendium chief business development officer Gareth Gadd said, “Our phones are with most of us most of the time these days. And their capabilities surpass the humble moniker of “phone”. We use them for mail, social media, searching the internet, playing games and much, much, more. However, it occurred to me the other day that I was using my personal phone for work as well as my private life. And I wondered whether that was a problem or not.”
Large companies have had Bring Your Own Device (BYOD) policies for a while now. As part of that policy they have control of the data on the BYOD device, whether it’s a phone or a laptop, and the policies especially cover emails and database access. They will also have password/access control policies such that if an employee changes companies their access terminates immediately, and the data removed from those devices. You get the idea. Large companies can afford experts to worry about these things and afford to deploy the necessary infrastructure.
A lot of smaller companies however can expect employees to bring their own devices because it is a huge cost saving to the business. This is especially so if your staff are not full-time e.g. volunteers, part-timers, interns etc. The problem here is that they have access to your systems. Now this doesn’t mean that you should treat your employees as though they are criminals; but what it does mean is that you should think about what data you hold, who has access and where that data is. Simple data privacy problems? Maybe.
Just suppose you have a data breach. How would you know who did it, how they did it and where they did it? Were they a “hacker” or was it an inside job? In the UK, the ICO (in specific circumstances) have fined a person who downloaded sensitive work files to their home machine (so that they could work from home) and on another occasion fined a person that continued to use IT systems of a previous employer (the person was also imprisoned). By not having policies in place and expecting your employees to use their own equipment you can lay your company wide-open to potential breaches. Risk minimisation.
Gadd said, “Going back to my phone predicament…I ended up having to buy a second phone, even though my phone was dual-SIM. That’s because there was no way of keeping my personal and my work data apart on my dual-SIM phone. Similar problems for laptops too.
“Our company has no BYOD policy and that’s because we don’t “do” BYOD. We really do believe that under the new data privacy laws that BYOD has the potential to mean Breach Your Own Data.”
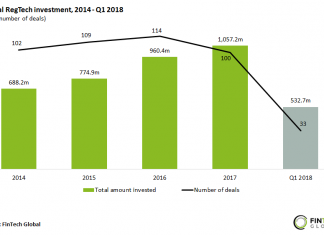
GDPR has been at the forefront of investors minds with the total volume of capital investments to GDPR-focused companies having exceeded $750m since 2104. This represents around 12.1 per cent of the total $6.1bn to be raised in the global RegTech sector, according to data by RegTech Analyst. GDPR is the third highest funding regulation in terms of startup funding between 2014 and 2018. Only KYC and AML solution providers, which received $2.1bn and $1.7bn respectively, have received a higher level of funding; however, GDPR is a much newer obstable facing financial institutions.
Copyright © 2018 RegTech Analyst