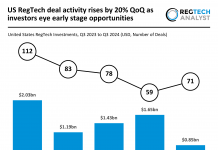
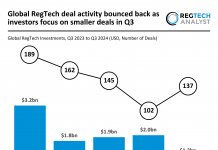
A researcher was rewarded a bounty after finding a massive security bug in PayPal’s login processes.
Alex Birsan, the researcher, earned a $15,300 bug bounty for his discovery.
He discovered the weakness in PayPal’s digital defences when he was looking at the FinTech giant’s authentication flow.
As Birsan went over it, he noticed a javascript file containing what appeared to be CSRF token and a session ID.
Still digging, Birsan found out that the CSRF token was used in the login security challenge. And that was where he found the weakness.
By failing to login a few times, users are required to solve a reCAPTCHA challenge before they can make another attempt.
If the Google CAPTCHA was solved, a HTTP POST request was initiated.
“The response to the CAPTCHA validation request is meant to re-introduce the user into the authentication flow,” Birsan said. “To this end, it contains a self-submitting form with all the data provided in the user’s latest login request, including their email and plain text password.
“I realized that, with the correct timing and some user interaction, knowing all the tokens used in this request was enough to get the victim’s PayPal credentials. In a real-life attack scenario, the only user interaction needed would have been a single visit to an attacker-controlled web page.”
By leveraging this bug on an infected website, hackers could get access to a PayPal user’s account after just one visit.
Birsan submitted his findings on November 18 and on December 10 he was paid his bounty. By the next day, PayPal had patched the vulnerability.
Copyright © 2018 RegTech Analyst