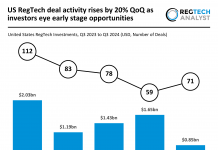
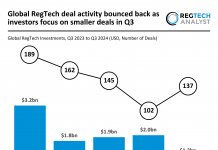
Only half of the vulnerabilities in cloud containers actually pose a threat, despite this, vast resources are being deployed to fix them.
Rezilion, an autonomous cloud workload protection platform, analysed the top 20 most popular container images on DockerHub and found 50% of the vulnerabilities were never loaded into memory and as a result, did not pose a threat. This is regardless of common vulnerability scoring system (CVSS) scores and despite the volume of resources in budget and manpower placed on fixing or mitigating them.
The IDC claims businesses spend 7-10% of their security budget on vulnerability management as daily operations rely more on cloud systems.
Rezilion claims vulnerability scanners overload and confuse security teams by uncovering too many results which are impossible to patch at once. Prioritization practises such as CVSS do not reduce breaches and firms with good security posture are breached just as much as those with bad security posture.
The cybersecurity company claims businesses can lower security budgets by triaging vulnerabilities through a continuous risk and trust assessment (CARTA) approach and prioritizing treatment of those most commonly targeted.
A study from Gartner suggests security and risk management teams should rate vulnerabilities based on risk. It also claims that by 2022 around 30% of enterprises will implement a risk-based approach.
Rezilion CTO and co-founder Shlomi Boutnaru said, “A vulnerability is only as dangerous as the threat exploiting it and in some instances during our research, we found the figure dropped to as low as 2%. By focusing on actual vs. perceived risk, we found the security industry has been unnecessarily exaggerating the number of vulnerabilities security teams must address, which has dangerous ramifications to the cloud security landscape.
“A continuous adaptive risk and trust assessment-based approach reduces friction and overhead by identifying vulnerabilities running in memory and then prioritizing treatment to those vulnerabilities commonly targeted by hackers as well as any that don’t have mitigations.”
Copyright © 2018 RegTech Analyst